Today, we will discuss about encryption and decryption. Many may be wondering what these are? These words can be seen while working on various topics related to hiding apps on mobile.

Encryption
Don’t go straight to the definition. Let’s talk before that. You must have heard the story of Alibaba. The cave door would open as soon as Alibaba uttered a magical speech. That is, Alibaba had a magical speech that was used as a safety measure inside of the cave for the diamond and jewelry. This story is very relatable with encryption and decryption.
Similarly, when we send our messages to someone online, they need a security code. Otherwise someone else can read this message if they want to. So, like the Alibaba’s magical word, we also add a keyword to the message and convert it into a magical or unreadable code.
Suppose I write “Hello”. That would be a code like “YRMS”. This process is called encryption. Your main message here is Plain text & the message after adding Security Code is Cipher text.
The basic function of encryption:
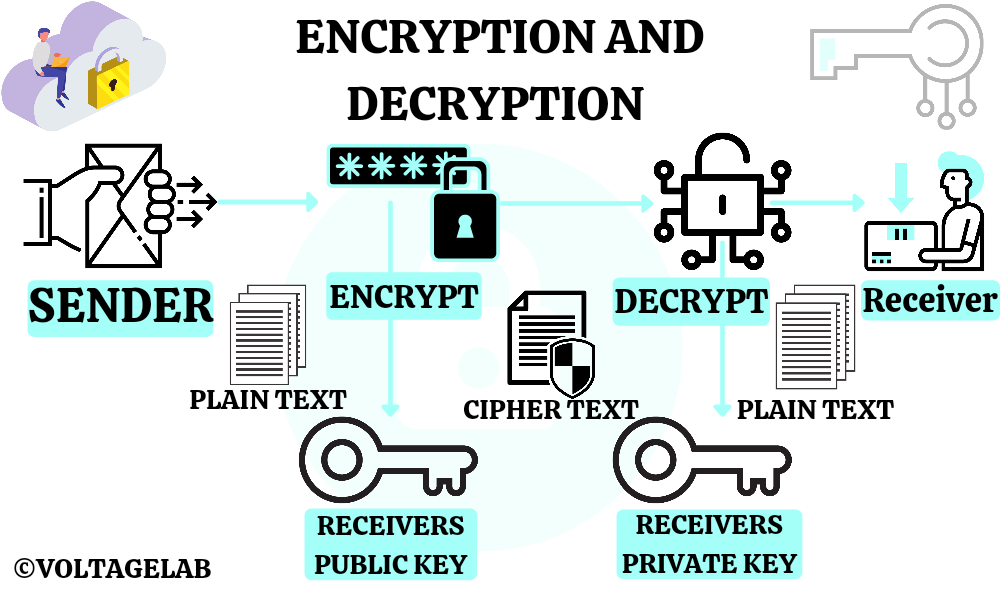
- To find any normal text
- Change it to cipher text
- Guarantees that if it is in the hands of a dishonest person, he should not be able to read the data.
There are basically three types of encryption. There are basically three basic methods of encryption. Each of them has its own advantages and disadvantages.
1. Hashing
2. Symmetric method
3. Asymmetric method
Decryption
Now let’s come to decryption. Here, it is only the reverse of Encryption. That code is converted to the original message and goes to the receiver. That is, the cipher text is converted to plain text. If you can catch the secret of this cipher text, you can claim yourself in as a hacker.

Some encryption techniques:
- Mono Alphabetic Cipher
- Hill Cipher
- Playfair Cipher
- Cieser Cipher
Check More Articles: